I recently went to a hotel, which unfortunately did not have free wifi. However it did have paid wifi. The wifi login page looked something like this. It had a place to put in the access code and also a place to get one. The place we are going to be focusing on is the access code. Here, we are looking to try and get wifi for free.
Reconnaissance
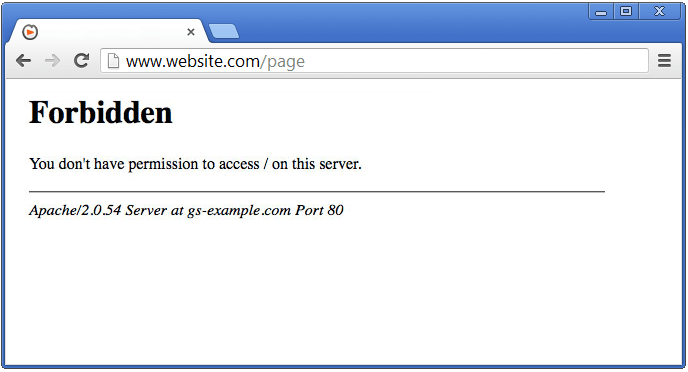
The first step in the process of ethical hacking is reconnaissance. Reconnaissance is extremely important. It’s the act of information gathering. This could mean things like what OS the server is running, and other things. So, if we look at the url up top, we can go to the index of that webpage, and even though we get a 401 response, we get something critical - At the bottom it shows us Red Hat Linux, which tells us that the server is running linux. Example for Apache:
Defining The problem
Just for this case, I’m going to create a webpage that can accept a code, and validates it. For the purpose of this video, I’m going to print any error messages. The backend for this website is written using Flask and SQlite, for the simplicity of this video. If you want to try it yourself, you can do it here.
Brute Force
The first thing that comes to mind would be to try every combination. However, this is definitely not a valid option. In our case, we have a string with a length of 4, but in a real case, the code would be 6 or mode characters. Let’s say we are using ASCII. The number of possible codes is $256^4$, which is about 4 billion. If each request takes a second to establish connection and send the form, which takes over 136 years. In reality, if they were using 6 characters it would take about 9 hundred thousand years. This makes trying every possible code not a valid option.

SQL Injection
Let’s try to be a little bit more smart. This is how the structure of the program could look. We have javascript and html on our browser, a flask api that connects to a SQL Database.
But first of all, what is a database? Think of a database as being an excel spreadsheet. We can have tables with rows and columns, and each of the columns have a name with the rows being the data. In this case, we can have a database with all the codes possible, which could look like this. SQL is a language that’s used for manipulating databases. It's incredibly popular, and our website uses it too. Let’s go over a few SQL statements.
The CREATE TABLE creates a table, like creating a spreadsheet in excel or google sheets. Here, you can specify the names for all the columns and the type of the data that goes in like INTEGER or TEXT. There is also something called private key. This means that the field is always unique.
CREATE TABLE 'Codes' (
'Room Number' INTEGER,
'Code' TEXT(4)
);
The INSERT INTO statement allows us to insert data into our database.
INSERT INTO 'Codes'
VALUES(,
703, '1XFF'
);
We can make queries with the SELECT statement. This is the most important one for us. For example, we can select all from a table.
SELECT * FROM 'Codes';
We can also select with some condition. In this case the select statement for our website could look like this.
SELECT * FROM 'Codes' WHERE Code='1XFF';
This changes based on what is inputted in the text field. The way we test for vulnerability is by entering the escape character ‘.
SELECT * FROM 'Codes' WHERE Code=''';
You can see how this statement would throw an error - The quote never completes itself. If the text is inputted into the sql statement without any validation, we can manipulate the statement to always return something. Such a SQL statement could look like this.
SELECT * FROM 'Codes' WHERE 1=1;
If we could get the SQL statement to look like this we would have successfully accomplished what we are trying to do. If we insert something like this, it successfully completes the statement.
SELECT * FROM 'Codes' WHERE Code='a' OR 1=1 OR 'a';
Let’s say that it could only be a number, the statement could look like this.
SELECT * FROM 'Codes' WHERE Code=1 OR 1=1;
Although we did this manually there are a lot of great tools to do all the work for us. For the Kali Linux distribution, you can use SQLMAP or SQLNinja to find which text fields are vulnerable, and perform the injection. There is also another tool called JSQL Injection which can make automated SQL Injections. Keep In mind, do not do this on any website in the real world. This post was for educational purposes only.